Updating the Machine Owner Key database
Machine Owner Key (MOK) is a security feature designed to protect the boot process of a computer system from unauthorized modifications or attacks. It is typically used in systems that support UEFI and Secure Boot, which require all bootloaders and kernel modules to be signed by trusted entities.
The MOK database is stored in a non-volatile memory location within the system’s firmware and contains a list of public keys that are allowed to sign the bootloaders and kernel modules. Each key in the MOK database is associated with a unique identifier and is used to verify the digital signature of the bootloaders and kernel modules. If a digital signature is valid, the boot process continues and the software is loaded. If a digital signature is not valid or the key used to sign the software is not in the MOK database, the boot process is halted and the system will not boot.
To enroll an MOK key, you must manually do so on each target system using the UEFI system console.
Because the key that you created is not included in the UEFI Secure Boot key database, you must enroll in the MOK database in the shim by using the mokutil command:
mokutil –import /etc/ssl/certs/pubkey.der
The previous command prompts you for a single-use password that you use when the MOK management service enrolls the key after you reboot the system.
Reboot the system
- The UEFI shim should automatically start the shim UEFI key manager at boot, as shown in the following figure. If you do not hit any key within 10 seconds, you will be unable to enroll your MOK key:

Figure 3.11 – Shim utility
Press any key to continue.
2. Then you should see the shim main menu. Select Enroll MOK from the menu.
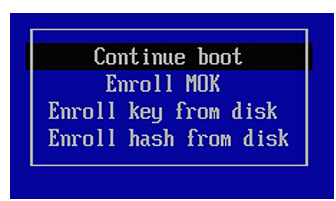
Figure 3.12 – Shim main menu
This will let you continue to enroll the key or view the key.
3. Select View key 0 from the menu (as shown in the following figure) to display the key details.
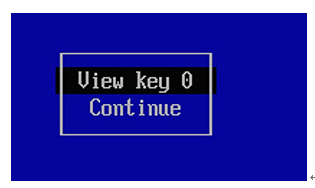
Figure 3.13 – View key
4. This will then display the key details. Verify that the values presented match the key you used to sign the module and that you inserted into the kernel image:
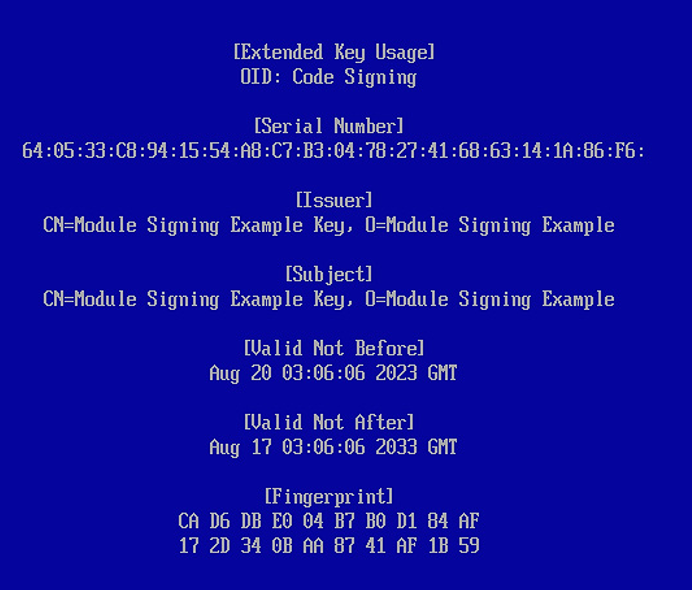
Figure 3.14 – Key details
Then press any key to return to the Enroll MOK menu.
- Select Continue from the menu.
- The Enroll the key(s)? screen is displayed, and you can now select Yes from the menu (as shown in the following figure).
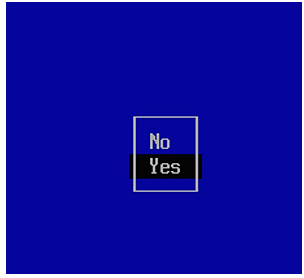
Figure 3.15 – Enrolling the key
Select Yes to enroll the key.
- You will then be prompted for a password. Enter the password you used when you imported the key using the mokutil command.
The key is enrolled within the UEFI Secure Boot key database. - You are now redirected to the main menu. Select Reboot from the menu.
Figure 3.16 – Reboot when done
How it works…
After booting the system, you can validate whether a key is included in the appropriate kernel keyring. Validation depends on the kernel version that you are running. Also, the keyring name that you need to check varies, as the implementation has changed across kernel versions.
If the key generated for signing custom modules is listed within the correct keyring, you can load modules signed with this key while in Secure Boot mode.
For RHCK on Oracle Linux 8 and UEK R6U3 kernels or later, keys within both the builtin_trusted_keys keyring and the platform keyring are trusted for both module signing and for the kexec tools, which means you can follow the standard procedure to sign a module and add it to the MOK database for the key to appear in the platform keyring, and it is automatically trusted.
Because a key can be loaded into the builtin_trusted_keys keyring, you should check both keyrings for the module signing key. Here’s an example:
[root@demo2 ~]# keyctl show %:.builtin_trusted_keys
Keyring
718980051 —lswrv 0 0 keyring: .builtin_trusted_keys
889527021 —lswrv 0 0 \_ asymmetric: Oracle CA Server: 23652876a2ec7c7794eb905265a1145e5ad5b873
643918572 —lswrv 0 0 \_ asymmetric: Oracle IMA signing CA: a2f28976a05984028f7d1a4904ae14e8e468e551
668816900 —lswrv 0 0 \_ asymmetric: Oracle America, Inc.: Ksplice Kernel Module Signing Key: 09010ebef5545fa7c54b626ef518e077b5b1ee4c
35441076 —lswrv 0 0 \_ asymmetric: Oracle Linux Kernel Module Signing Key: 2bb352412969a3653f0eb6021763408ebb9bb5ab
[root@demo2 ~]# keyctl show %:.platform
Keyring
858046056 —lswrv 0 0 keyring: .platform
886150219 —lswrv 0 0 \_ asymmetric: Oracle America, Inc.: 430c85cb8b531c3d7b8c44adfafc2e5d49bb89d4
698748825 —lswrv 0 0 \_ asymmetric: Oracle America Inc.: 2e7c1720d1c5df5254cc93d6decaa75e49620cf8
790695213 —lswrv 0 0 \_ asymmetric: Oracle America, Inc.: 795c5945e7cb2b6773b7797571413e3695062514
227851788 —lswrv 0 0 \_ asymmetric: Oracle America, Inc.: f9aec43f7480c408d681db3d6f19f54d6e396ff4